Cybersecurity risks have been prevalent ever since technologies started playing a crucial role in running a business. And with the ever-increasing complexity of business operations, companies are focused on building robust cybersecurity strategies for risk mitigation. The NIST Cybersecurity Framework (CSF), as mentioned in our previous article in this series, provides a systematic approach to risk assessment for enterprises to safeguard their systems and data proactively. The core guidelines of the NIST framework cover the entire lifecycle of a company’s cybersecurity management process, from identifying to recovering from a cyber-attack.
NIST CSF Functions: Key Objectives and Guidelines
The NIST CSF Framework is critical in setting standards and making recommendations to protect businesses from unexpected risks. Here are the five core cybersecurity functions of the NIST framework:
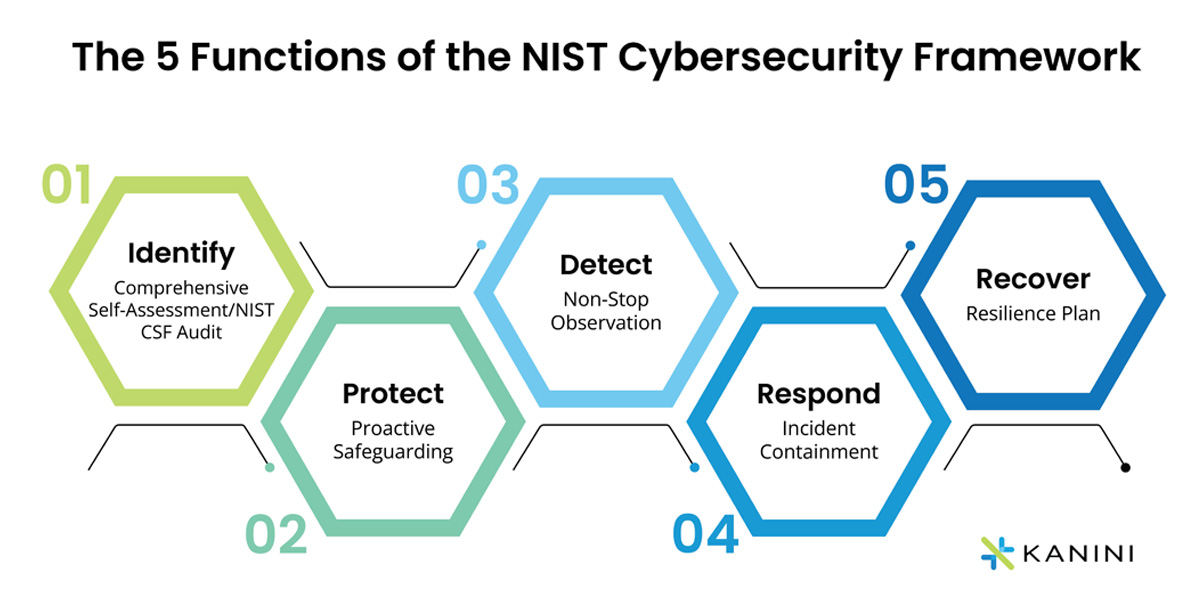
1. Identify - Comprehensive Self-Assessment/NIST CSF Audit
2. Protect - Proactive Safeguarding
3. Detect - Non-Stop Observation
4. Respond - Incident Containment
5. Recover - Resilience Plan
The ‘Recover’ function is the final core function of the NIST cybersecurity framework. Cybersecurity incidents may cause broken business processes, and the enterprise should focus on restoring its capabilities. Whether it is recovering lost data or fixing applications, companies should make sure that the recovery process is quick. When the recovery takes time, it can bog down clients and cause attrition. NIST stresses the importance of learning from the flaws in the system with each cybersecurity incident to expedite the recovery process.
Laying the Foundation with NIST CSF Audit
The Way Forward
Author

Joshua Smith
Joshua is a process improvement thought leader and digital transformation expert at KANINI. Over the past 15 years, his focus has always been on achieving organizational maturity and enhancing business processes through implementing tools and workflows to drive transformation initiatives. With experience in multiple verticals from – manufacturing to healthcare, Joshua brings a practitioner’s perspective when working on business solutions and goals to allow him to advise and guide on industry and process best practices.








