Organizations require constant re-thinking and innovation that matches their customer demand but also scales without roadblocks. Implementing new solutions and technologies is often accompanied by problems and vulnerabilities with your IT infrastructure security. For instance, the new cloud migration you did could be exposing you to outside threats. If we fail to assess the security dangers that come up when new points of exposure, like new laptops, are introduced into your system, this could result in a complete failure of our security strategy. You cannot even afford to be exposed in between your scheduled scanning process.
Critical vulnerabilities often hide under the radar of security challenges today. When exploited, the lack of effective vulnerability response can result in a major impact to business reputation and data security. It doesn’t help that breaches are becoming more and more severe. Methods to exploit vulnerabilities are getting more sophisticated, with cybercriminals increasingly leveraging AI and ML to thwart traditional vulnerability response mechanisms. Having a solution which interlocks all components —security, risk, and IT— is crucial to stay ahead of these tactics and take a holistic approach to vulnerability response.
While this is easier said than done, the need for its complete efficiency has never been more crucial.
The ServiceNow Solution
ServiceNow® SecOps Vulnerability Response helps you respond faster and more efficiently to threats by connecting security and IT teams, and providing real-time visibility. It connects the workflow and automation capabilities of the Now Platform® with vulnerability scan data from leading vendors to give you a single platform for response that can be shared between both security and IT.
The ServiceNow Security Incident Response application tracks the progress of security incidents right from discovery and initial analysis, through containment, eradication, and recovery, and into the final post-incident review, knowledge base article creation, and closure.
Vulnerability Response provides a comprehensive view of all vulnerabilities affecting a given asset or service through integration with ServiceNow Configuration Management Database (CMDB), as well as the current state of all vulnerabilities affecting the organization. When used with the CMDB, Vulnerability Response can prioritize vulnerable assets by business impact, using a calculated risk score so that teams can focus on what is most critical to the organization.
With better visibility, teams can respond more efficiently, reducing both the vulnerability backlog and your risk exposure.
Want to protect your organization from data breaches efficiently and mitigate your reputational risks? Get a free consultation with our ServiceNow experts
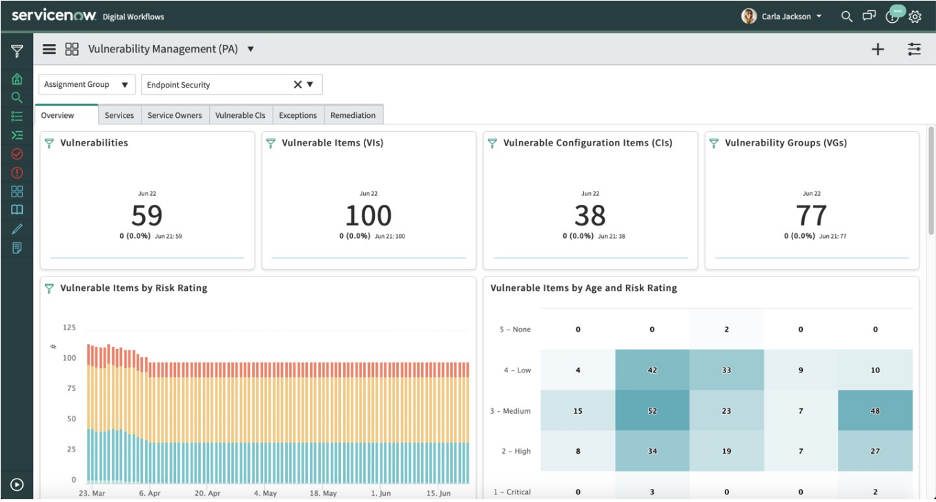
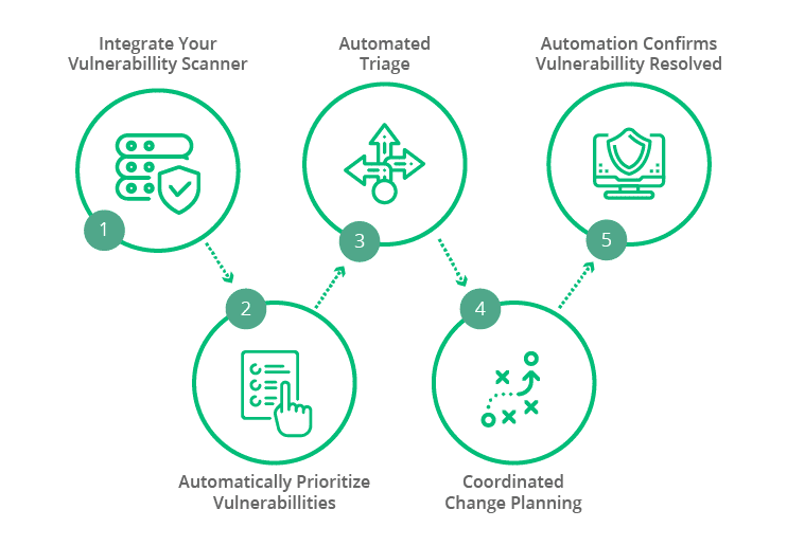
Automated Vulnerability Response
ServiceNow Vulnerability Response enables quick remediation of threats by automating the import and grouping of vulnerable items according to group rules. Vulnerability data is pulled from internal and external sources, such as the National Vulnerability Database (NVD) or third-party integrations.These applications work in parallel to make your IT department faster and more efficient at threat response.
When critical vulnerabilities are found, Vulnerability Response can automatically initiate an emergency response workflow that notifies stakeholders and creates a high-priority patch request for IT. To ensure accuracy in patching, Vulnerability Response recommends the most impactful remediation activities with ServiceNow SecOps Vulnerability Management. Analysts can monitor real-time status of the patching progress and ensure process visibility across security and IT. It also optimizes remediation by using machine learning to identify the most appropriate teams for vulnerability findings and auto-assignment of tasks.
Make Use of Threat Intelligence
A lack of visibility into IT infrastructure, services and solutions has led businesses into a lot of security mishaps. There are real challenges in handling the onslaught of threats in real-time since the Security and the IT teams spend considerable time trying to precisely identify vulnerabilities, reasons behind those vulnerabilities and then respond to it accurately. The ServiceNow Threat Intelligence provides a reference point to the Structured Threat Information Expression (STIX) data with the help of artificial intelligence and machine learning.
Monitor Performance Analytics
You can make faster, better-informed decisions when you have a single, consolidated view of the environment and accurate, comprehensive data at your fingertips. Automated reporting using ServiceNow® Performance Analytics for Security Operations helps us stay well informed, track progress over time to pinpoint areas for improvement, and demonstrate security compliance to audit teams.
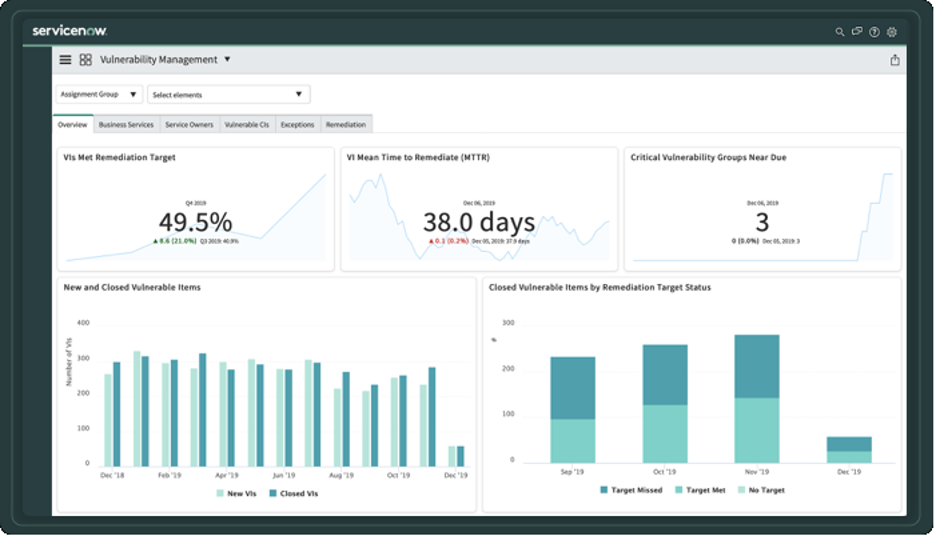
Streamlining Security Incident and Vulnerability Response is inevitable to creating a coordinated remediation strategy for vulnerabilities. For more information on how you can leverage ServiceNow’s Vulnerability Response application, drop us a message.
Author

Joshua Smith
Joshua is a process improvement thought leader and digital transformation expert at KANINI. Over the past 15 years, his focus has always been on achieving organizational maturity and enhancing business processes through implementing tools and workflows to drive transformation initiatives. With experience in multiple verticals from – manufacturing to healthcare, Joshua brings a practitioner’s perspective when working on business solutions and goals to allow him to advise and guide on industry and process best practices.








