
Better Workflows Leading to Best Outcomes
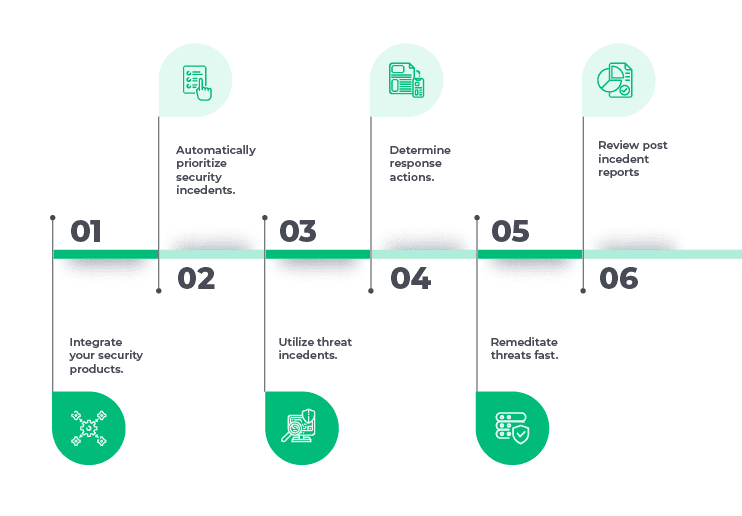
Security Incident Response (SIR)
Configuration Compliance
Vulnerability Response
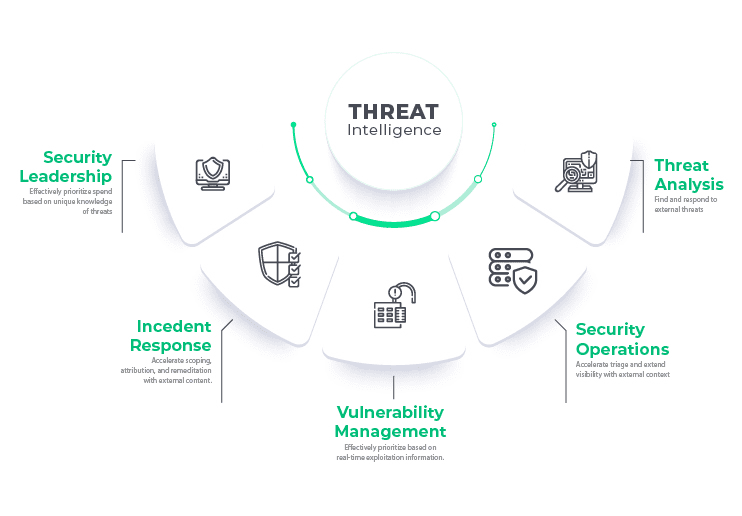
Threat Intelligence
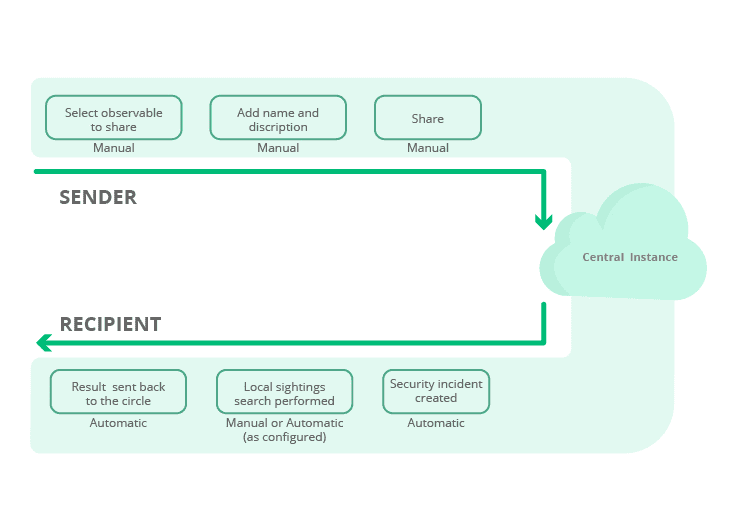
Trusted Security Circles
DLP Incident Response
Deep IT Integration
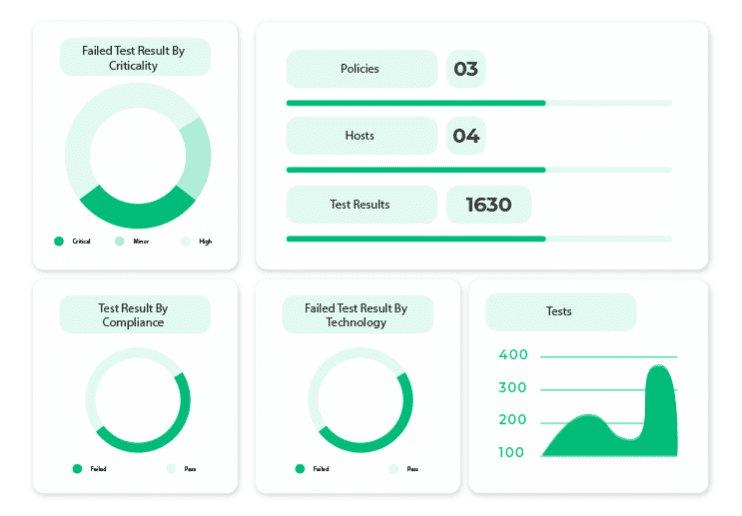
Benefit from a Secure Configuration Assessment (SCA) application that aggregates scan results from integrations with configuration scanning applications. Prioritize configuration compliance issues using the Configuration Management Database (CMDB) and tightly integrate with IT change management processes to remediate non-compliant configurations. By matching failed configuration tests with assets, prioritizing based on severity and criticality, and facilitating swift remediation through workflows, configuration compliance empowers organizations to proactively manage risks and enhance cybersecurity posture.
ServiceNow Configuration Compliance works with third-party SCA scanner applications and integrates with ServiceNow GRC Governance, Risk, and Compliance for continuous monitoring.


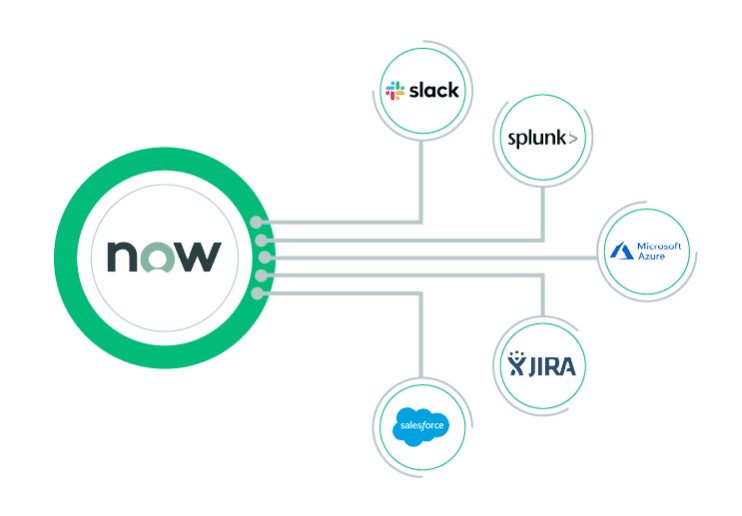

Benefit from a Secure Configuration Assessment (SCA) application that aggregates scan results from integrations with configuration scanning applications. Prioritize configuration compliance issues using the Configuration Management Database (CMDB) and tightly integrate with IT change management processes to remediate non-compliant configurations. By matching failed configuration tests with assets, prioritizing based on severity and criticality, and facilitating swift remediation through workflows, configuration compliance empowers organizations to proactively manage risks and enhance cybersecurity posture.
ServiceNow Configuration Compliance works with third-party SCA scanner applications and integrates with ServiceNow GRC Governance, Risk, and Compliance for continuous monitoring.








Insights. Alcove Of Resources.
Automation, Cloud, AI-driven Insights – more than “Dreams of the Future” these have become the “Demands of the Present”, to set the stage for a business to be truly digital.


Our Services
Contact Us
Newsletter

| Cookie | Duration | Description |
|---|---|---|
| cookielawinfo-checkbox-analytics | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Analytics". |
| cookielawinfo-checkbox-functional | 11 months | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Functional". |
| cookielawinfo-checkbox-necessary | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Necessary". |
| cookielawinfo-checkbox-others | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Other. |
| cookielawinfo-checkbox-performance | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Performance". |
| viewed_cookie_policy | 11 months | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |