Welcome back! In our previous post on the NIST Cybersecurity Framework (CSF), we explained how the core functions of the framework act as universal guidelines for enhancing an enterprise’s cybersecurity practices. In this post, we’ll go over how an enterprise is categorized based on the NIST CSF assessment. When it comes to cybersecurity, there is no guarantee that a company is completely safe. It all depends on the measures it takes. Therefore, security leaders of companies must prioritize conducting a cybersecurity readiness assessment to identify the flaws in their cybersecurity practices and develop a robust strategy to go up the maturity curve.
NIST CSF Readiness Assessment - Its Stages
Reshaping the cybersecurity landscape of a company is important to ensure that the business can create value consistently. The NIST CSF assessment is aimed at helping CISOs and security teams understand their enterprise’s cybersecurity maturity level. The assessment provides a structured approach around each of the core functions to get an overall understanding of where that company stands in terms of cybersecurity management.
The results of the NIST CSF risk assessment classify companies into the following four categories:
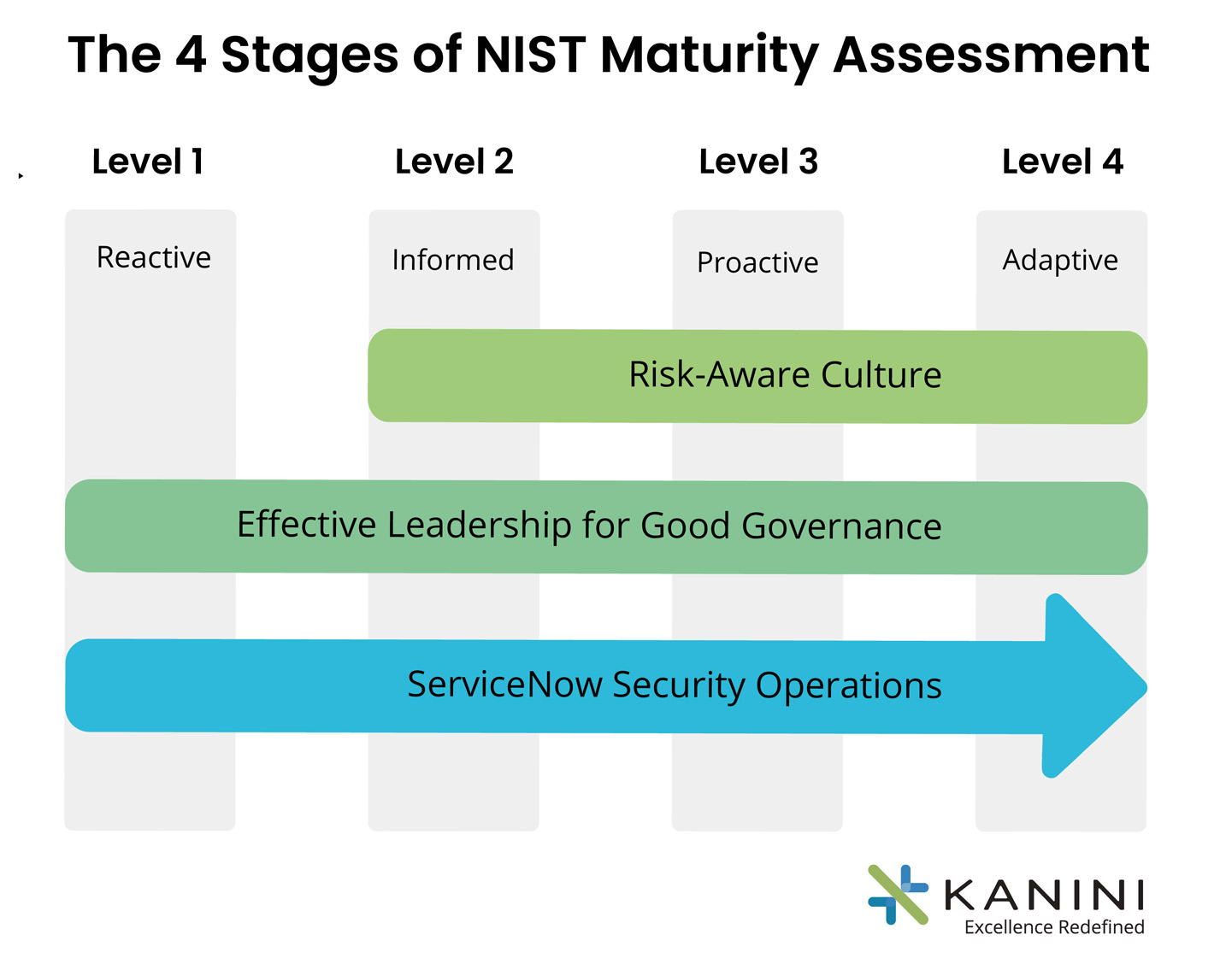
Level 1 - Reactive
Level 2 - Informed
Level 3 - Proactive
Level 4 - Adaptive
ServiceNow Security Operations (SecOps) - End-to-End Cybersecurity Solution
- Quick Response to Security Incidents: Companies can leverage automation to cater to and resolve security incidents within a short time.
- Detailed Guidance on Solving Cybersecurity Incidents: Security teams can get their hands on playbooks that can provide guidelines on how common security incidents can be resolved.
- Prompt Prediction of Cybersecurity Threats: Enterprises can predict adversary tactics and prevent potential cybersecurity incidents with the MITRE ATT&CK framework.
- Easy Resolution of Application Vulnerabilities: The security risks involved during the development stage of applications can be resolved easily through continuous monitoring processes.
- Advanced Cybersecurity Insights to Stakeholders: Security teams can explain the state of the company’s security and the investments required through advanced analytics dashboards.
Final Words
Author

Joshua Smith
Joshua is a process improvement thought leader and digital transformation expert at KANINI. Over the past 15 years, his focus has always been on achieving organizational maturity and enhancing business processes through implementing tools and workflows to drive transformation initiatives. With experience in multiple verticals from – manufacturing to healthcare, Joshua brings a practitioner’s perspective when working on business solutions and goals to allow him to advise and guide on industry and process best practices.








